Attackers have exploited a vulnerability in the Opyn ETH Put contract to walk away with more than $370,000.
One of the first members of Crypto Twitter to report on the theft, DegenSpartan, stated on Aug. 4 that the traders used flash loans to buy Ethereum Put oTokens (oETH) from Uniswap. They then reportedly chose an ERC20 token — in this case, USD Coin (USDC) — as collateral and exercised the trading option.
The result was reportedly a double transfer which effectively “stole” the collateral. According to blockchain records, the attackers received both their original Ethereum (ETH) deposits and USDC options.
In a Aug. 4 blog from Opyn, the platform estimates losses from the exploit at 371,260 USDC but said this amount may change.
“This exploit allowed an attacker to ‘double exercise’ oTokens and steal the collateral posted by certain sellers of these puts.”
Pulling liquidity quickly
Opyn realized something was happening within the day and issued a statement on Twitter, saying it had removed liquidity from Uniswap during its investigation.
Hey all, it seems like there has been an issue with some oTokens contracts. We are working hard on understanding this issue so we can let help users as best we can. We have removed liquidity from Uniswap in the mean time. Would be best to not open new vaults at the moment.
— opyn (@opyn_) August 4, 2020
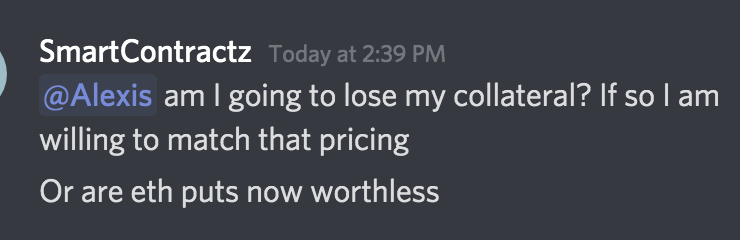
Attempting to prevent further abuse of this loophole, Opyn recovered 439,170 USDC of collateral from outstanding vaults using a white hat hack, effectively returning it to Put sellers. However, some users were still understandably upset at the loss and delayed response:
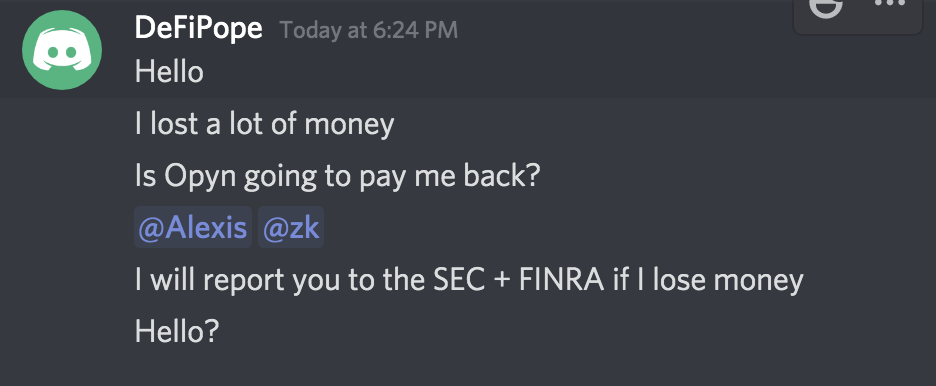
Screenshots from Opyn Discord chat
According to Opyn co-founder Alexis Gauba in a Discord chat session, the platform has offered to buy any ETH Put oTokens “at above market prices,” which she said were 20% above the best ask price at Deribit.
“This only applies to oTokens that were bought before today,” Gauba said. The last update she posted stated Opyn was working on a plan “to mitigate impact for ETH put sellers.”



Comments (No)